| News Details |
An improved robust image watermarking scheme based on the singular value decomposition and genetic algorithm
2022-04-11
Atheer Bassel1, Md Jan Nordin2
1University of Anbar, Iraq
2 Center for Artifical Intelligence Technology, Faculty of Information Science and Technology, Universiti Kebangsaan Malaysia, 43600 Bangi, Selangor Darul Ehsan, Malaysia.
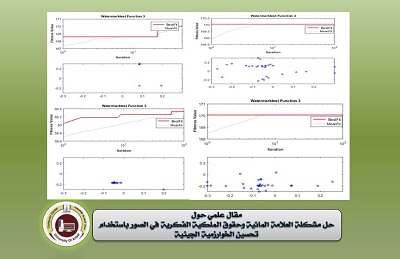
This paper propose a robust image watermarking scheme based on the singular value decomposition (SVD) and genetic algorithm (GA). SVD based watermarking techniques suffer with an issue of false positive problem. This leads to even authentication the wrong owner. Prevention of false positive errors is a major challenge for ownership identification and proof of ownership application using digital watermarking. We employed GA algorithm to optimize the watermarked image quality (robustness) of the extracted watermarks. The former can be overcome by embedding the owner’s components of the watermark into the host image, the latter is dependent on how much the quantity for the scaling factor of the principle components is embedded. To improve the quality of watermarking (robustness), GA is used for optimize the suitable scaling factor. Experimental result of the proposed technique proves the watermark image ownership and can be reliably identified even after severe attacks. The comparison of the proposed technique with the state of the art show the superiority of our proposed technique where it is outperforming the methods in comparison.