| News Details |
Data Security Using Random Dynamic Salting and AES Based On Master-Slave Keys For Iraqi Dam Management System
2022-08-07
Hussam J. Ali 1, Talib M. Jawad2, Hiba Zuhair3
1 Informatics Institute for Postgraduate Studies, Iraqi Commission for Computers and Informatics, Baghdad, Iraq
2 College of Information Engineering, Al-Nahrain University, Baghdad, Iraq
hiba.zuhir@coie-nahrain.edu.iq
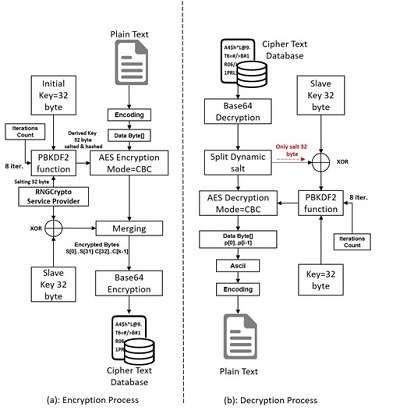
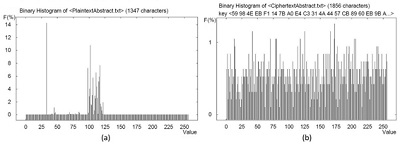
Nowadays, data security is one of the critical challenges of e-government in Iraq, as it needs IT infrastructure, data integrity, and user privacy protection against Internet threats that render this vital infrastructure ineffective. This paper deals with a multi-level secure model by encrypting and decrypting the data using the Advanced Encryption Standard (AES) algorithm with keys derived via PBKDF2 sequence generator, RNG, and a secondary key to protecting the random generator also to protect the main string. The empirical analysis of encryption/decryption process speed, plain text sensitivity, cipher text analysis, key space analysis, and histogram analysis was conducted. The results of the proposed model showed the level of obstruction of known attacks such as brute force attacks, statistical, and differential attacks. Thus, the encryption model can be implemented in information management systems and in the application of electronic governance, for example, dam data management systems.